Why Is Address Resolution Protocol Poisoning Possible?
ARP poisoning is possible because ARP, as a protocol, does not have any type of security. It is simply not designed to be secure. Devices on the internal network receive and modify their own ARP caches without any authentication or encryption. This allows an attacker to send self-created ARPs to any device on the local network. When this happens, the devices process ARPs as if they came from a trusted source. Because of this, we have no defenses against this type of attack. You can read more about the mechanism of ARP in detail in my previous post.
The Poisoning Process
Source: Author's own
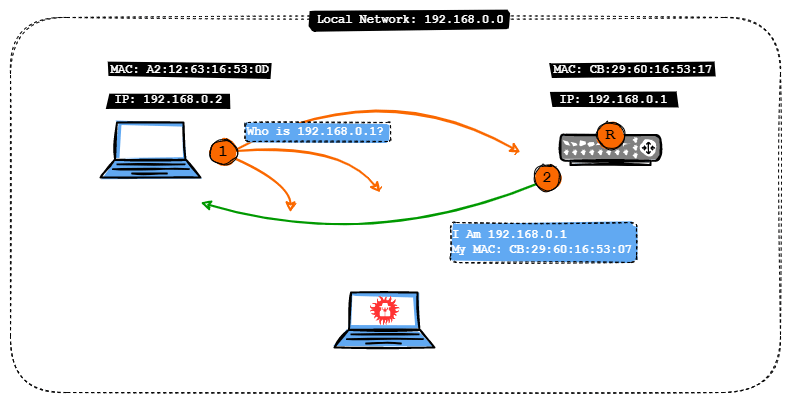
The picture above shows a laptop communicating with a router on the local network. The laptop has an IP address of 192.168.0.2 and the router has an IP address of 192.168.0.1. The MAC addresses of the laptop and the router are also shown in the illustration. It is a necessary piece of information to demonstrate the ARP poisoning process. The first time you connect your laptop to the network, it needs to know the router's MAC address. As it only knows the IP address of the router, it sends an address resolution protocol request to everyone on the internal network asking who 192.168.0.1 is . As the router is also on this local network and sees all such requests, it responds to the requesting laptop by sending its MAC address. The requesting laptop then stores this information in its own ARP cache.
Source: Author's own
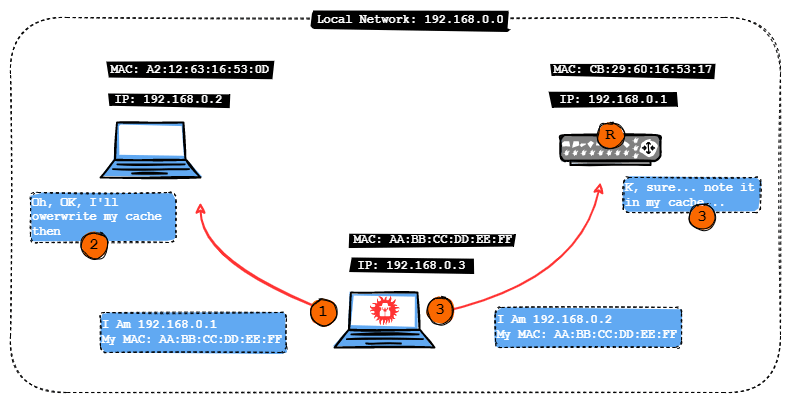
For an effective Man-In-The-Middle (MITM) attack that uses ARP poisoning, the attacker must be on the same local network as the victim. In the example I used, the attacker's IP address is 192.168.0.3 with the MAC address indicated in the picture. To accomplish ARP poisoning, the attacker sends an ARP response message to the target device. This is known as "poisoning" since it is unsolicited information. Because ARP is not subject to any technological security restrictions or constraints, the recipient device is compelled to handle such messages.
In the above scenario, the victim gets the ARP message and modifies the information in their cache. From then on, if the victim had any message coming to the 192.168.1.1 IP address, it would not go directly to the router, but straight to the attacker's MAC address. Now that the victim's laptop has been poisoned with a bogus MAC address, the attacker is doing the same to the router. Once the poisoning has been carried out on both sides, all further communication between the two devices will proceed through the attacking device.
The MITM attack is hard to execute because attackers must be on a local network that is not always accessible to them. It would be considerably easier if the attacker and the victim were both using the same computer.
Conclusion
ARP spoofing has been used by hackers for more than 30 years. Attacks using poison might be carefully planned or executed in response to a situation. Opportunity attacks include stealing data from WiFi networks that are left exposed to the public, whereas planned attacks include things like denial of service (DOS) attacks. Even though these exploits can be stopped, they are still used a lot because they are easy to do both technically and financially.
